Best Practices: Risk Assessment Strategy
While organizations are striving to prevent as many threats as possible by enabling strict security policies, the bad actors—outside intruders or rogue insiders—are one step ahead. New hacking and phishing methods are introduced every now and then, the malware becomes harder to recognize, and unnoticed identity theft wins over brute force attacks and remains concealed longer. Risks are everywhere and it seems like they stretch far beyond computers and networks. Actually, the risk is just anything that distracts your company operations, leads to potential loss, or negatively impacts the company in any way.
While preventing risks should be your motto, establishing an adequate response framework is equally important. In this article, you will learn a technique for assessing risks and get some tips on how to set up a risk mitigation plan.
While this article focuses on assessing information security- and compliance-related risks, the technique itself applies to risks in general. The strategy consists of the following steps that are essential if you want to secure your organization and create an effective framework that would allow you to address risks in a timely manner.
- Identifying Risks
- Evaluating Risks
- Prioritizing Risks
- Knowing When Risk Is on Radar
- Creating a Risk Management Plan
Your goal is to create a spreadsheet where for each risk listed you can clearly see its warning signs and how they are tracked, remediating steps with employees in charge. See Bonus—Example from a Risks Spreadsheet.
Identifying Risks
As simple as it sounds, start by creating a risk inventory. In a spreadsheet, write down all risks you can think of. These risks can be related to any sphere of the company's life. For example,
- Assets. The risks related to assets may include potential data loss due to files being occasionally or purposely deleted, data stealth and disclosure (internal or external), industrial espionage, malware, etc.
- Operations. The risks related to company operations may include identity theft, privilege abuse when someone with excessive rights starts performing actions outside his or her scope of responsibility.
- Physical/environment. Any nature- or human-related risks such as fire destroying the server room or a sudden illness of a key employee.
- Technology/industry/government. This risk category may include constraints related to outside changes and trends. For example, the technology you currently rely on may fail, the government may introduce a new regulation , therefore you'll have urgently update your policies and procedures.
For sure there are risks that cannot be foreseen and that's okay. If you thoughtfully did the analysis, the scenarios you have written in your inventory spreadsheet should be enough to cover the vast majority of risk situations.
Evaluating Risks
Once you have the risks written down, take a closer look at them. Do these risks have an equal impact on your organization? Are they likely to happen with the same frequency? Probably they are not. Each risk is unique, some risks are very severe but you do not expect them to happen so often while others are minor but you are likely to deal with them almost every week.
In your spreadsheet, add the risk severity and probability columns. Determine severity and probability for each risk you listed—fill columns with values ranging from low to high. For now, you can start with the range of three values but later you can expand your model to include up to 5 levels of severity and probability.
To give you a little bit more understanding, here is the example:
|
RISK |
SEVERITY |
PROBABILITY |
|---|---|---|
|
Operations: |
|
|
|
Privilege misuse |
medium |
high |
|
Identity theft (with industrial espionage) |
high |
medium |
|
Environment: |
|
|
|
Electricity outage in data center |
medium |
low |
The values you assign are typically based either on industry best practices or on your current policies and security controls. By all means, these values should make sense to your specific organization.
Prioritizing Risks
You did a great job analyzing the risks, their impact and likelihood. It's time to make things a little bit more visual and colorful. Here comes the risk matrix—it helps to categorize and prioritize risks based on the zone they fall into.
The risk matrix has the risk probability (low to high) on the X axis and severity (low to high) on the Y axis. It forms 9 zones that are divided into three categories. Look at the risks you listed and determine the category each risk belongs to. For example, the risk with a high severity and medium probability will fall into the red (p. 1 critical) category.
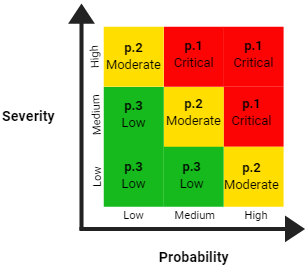
Priority 1. Critical: The risks with a high probability or high severity, or both are considered critical. You may expect them to occur sooner or later and they'll definitely have a huge impact on your company.
Priority 2. Moderate: The risks that are a mixture of low's and high's or two mediums are known as moderate. They are either frequent but do not affect your organization seriously or are pretty rare but more hazardous.
Priority 3. Low: Other risks. Although these risks might have a significant impact on the company, they are pretty random. In some case, you cannot help them anyway or have a very limited control over them (e.g., fire destroying the office building). This category also includes minor risks that won't necessarily lead to bad consequences.
Now, you can color code your risk spreadsheet to show risk priorities.
Knowing When Risk Is on Radar
Knowing your risks and prioritizing them is not enough for successful risk mitigation. You should know exactly when the risk is emerging. The faster you qualify certain actions as risk, the faster you can respond and take the situation under control. To facilitate risk recognition, create a formal list of signs indicating the emerging risk and decide how you are going to track them.
You can train your personnel to monitor the warning signs with Cygna Auditor. For example, configure alerts for suspicious actions or changes affecting business critical assets, set a review schedule for compliance reports, and run searches to identify activity peaks. With Cygna Auditor, you can turn vague risk indicators into tangible alerts and search queries.
Creating a Risk Management Plan
We are finally approaching the risk management part! Now you know everything about your risks; it's high time to decide how you are going to handle them. Coming up with the risk management plan in advance is essential if you want to remediate risks effectively and in the fastest way possible.
Since the risks are different, they should be handled differently. For each risk level, you can come up with a general strategy and then break it down to tangible controls for each risk individually.
For example, you don't need to plan something specifically for Priority 3 (Low) risks. These risks are either random or insignificant, just keep track of them. A good idea is to schedule regular checkups—every month or week depending on resources available in your department—and stay tuned.
Risks of the Priority 2 (Moderate) group require more attention and planning. There is no doubt you'll want to monitor the warning signs and have a remediation plan in hand. For each risk situation, you can set up recommended recovery or mitigation steps you and your colleagues can follow. Some moderate risks can be addressed in bulk as you are doing your routine administration chores (e.g., resolving permissions conflicts, managing lockouts).
The risks to focus on are the risks from the Priority 1 (Critical) group. They are pretty severe and you can expect them to happen at any moment. Why not get ready and face them being prepared? Here two recommendation for building an effective risk management plan.
- Proactively work towards preventing these risks. If you make your best to avoid risks in the first place, you'll decrease their probability and save time on monitoring. Just an example, it's easier to limit user permissions on shared folders than to investigate data distribution reports looking for a possible data theft or suspicious activity, right? Most risks can be eliminated or at least reduced by following simple best practices and enforcing basic security controls. Most likely, you have already adopted these security procedures in your organization. So go forward and map them to the risks you identified. Soon you'll find out that just a bunch of security controls covers most of Priority 1 risks.
- Have a detailed instruction-like response plan and personnel assigned to perform certain actions. When you notice the risk, first and foremost don't panic. While under tension, we all tend to forget obvious things, so having a step-by-step plan right in front of you can help you a lot and reduce your stress level. Prepare the list of steps in advance and decide who is responsible for what. Certainly, there are risks you cannot address as a security officer or internal auditor, so do not hesitate to delegate the custody of the risk tracking and mitigation to appropriate employees. For example, the legal department can review recent changes to compliance regulations, the accountants can track changes to the taxation system, and Active Directory admin can restore deleted objects from tombstones. Once each involved employee has a clear understanding of his or her duties, it's much easier to handle risks. Should the risk occur, those who are in charge of on-going monitoring will identify the risk and contact their fellow co-workers to take care of it. At the end of the day, working in a team where everyone knows what to do is just less stressful for employees and overall beneficial for the company.
In both cases, use Cygna Auditor to collect detailed information and keep risks on your security radar. Configure Cygna Auditor to be notified on critical changes, save your search queries as custom reports and review them according to the agreed schedule.
Bonus—Example from a Risks Spreadsheet
|
RISK |
Identity theft | ||||||||||||||||||||||||||||
|
LEVEL |
1. Critical | ||||||||||||||||||||||||||||
|
SIGNS OF EMERGING RISK |
|
||||||||||||||||||||||||||||
|
REMEDIATION PLAN |
Avoiding risk—proactive security:
In case of risk:
|
Summary
Now you've learned the basics of risk management. You can analyze risks specific to your organization and present them in a form of a spreadsheet where each risk is prioritized, its indicators are clearly described, monitoring is planned, and the remediation plan includes instructions for involved personnel.
Risks are an inevitable part of our lives. And though having a risk management plan at hand cannot save you from actual risks happening, it allows you to know your environment better and provide a fast response to risks if they occur. Identifying early signs of threats shortens the gap between the actual threat action and your response and helps you minimize the potential damage while following security best practices can significantly reduce the risks in the first place.
