Ports and Network Resources Reference
Check this reference and ensure your firewall is configured to allow inbound and outbound connections to the following ports. This port configuration is essential to product operability since it facilitates data collection, acquisition, and transmission between the product components and audit sources.
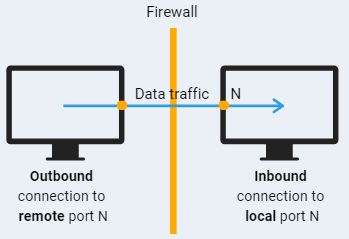
QUICK TIP: Need a quick recap of how the firewall works? For successful data transmission through the firewall, the sender computer should be allowed to transfer data (outbound connection) to a specific port on a remote computer. On the other side, the receiver computer should be configured to allow traffic (inbound connection) to the same local port. The best practice is to keep inbound connections all under supervision and not to open ports unless necessary.
- Start the Windows Firewall with Advanced Security.
- On the left, specify the type of rule you want to create (inbound or outbound), right-click the section, and select New Rule.
- Complete the wizard as follows:
- On the Rule Type step, specify Port.
On the Ports and Protocols step, select the protocol type (TCP or UDP). Depending on the rule you create, specify the port number in the Specific local ports or Specific remote ports correspondingly.
- On the Action step, select Allow the connection.
- On the Profile step, specify when this rule should be in use (within your corporate domain, private network, or public network).
- On the Name step, enter the name and description explaining the rule.
- Ensure the newly created rule is enabled.
Cygna Auditor Platform
The server or workstation where the Cygna Auditor platform is deployed should be configured to allow the following connections.
|
CONNECTION |
PORT |
PROTOCOL |
PORT |
REQUIRED FOR |
|---|---|---|---|---|
|
Inbound |
Local |
TCP |
80 (http) 443 (https) |
IIS |
|
Outbound |
Remote |
TCP |
135 |
RPC |
|
Outbound |
Remote |
TCP |
1433 |
Interaction with Cygna Auditor SQL Server-based data storage. |
|
Outbound |
Remote |
TCP |
443 (https) |
Access to Cygna Auditor online help at docs.cygnalabs.com. Agent-based Active Directory data collection: *.core.windows.net (GET) msdl.microsoft.com msdl.microsoft.com/download/ Interactions with Microsoft 365: cygnacloud.azurewebsites.net (GET and POST) graph.microsoft.com (GET only) login.microsoftonline.com (GET only) login.windows.net (GET only) *.microsoftonline-p.com (GET only) manage.office.com (GET only) management.azure.com (GET only) Interactions with AWS: *.amazonaws.com (GET and POST) If you have a proxy server configured in your environment, it should as well allow connections to these URLs. Also, the computer from which you configure Microsoft 365 data collection ("authorize") should allow connections to these URLs. |
SQL Server-Based Data Storage
The server where SQL Server instance with collected audit data is located should be configured to allow the following connections.
|
CONNECTION |
PORT |
PROTOCOL |
PORT |
REQUIRED FOR |
|---|---|---|---|---|
|
Inbound |
Local |
TCP |
1433 (default instance) dynamic (named instance) |
Interaction with Cygna Auditor platform |
Active Directory DCs
Domain controllers in the Active Directory domain you want to audit should be configured to allow the following connections.
|
CONNECTION |
PORT |
PROTOCOL |
PORT |
REQUIRED FOR |
|---|---|---|---|---|
|
Inbound |
Local |
TCP |
135 and dynamic* |
Interaction with Cygna Auditor platform. |
|
|
Note: * In Windows Firewall, it is recommended to enable the RPC and RPC-EMAP firewall rules. |
|||
|
Outbound |
Remote |
TCP |
1433 |
Interaction with Cygna Auditor SQL Server-based data storage. |
|
Inbound |
Local |
TCP |
445 |
Access to the C$ share for agents. |
|
Inbound |
Local |
TCP |
139 |
Only required for networks relying on NetBIOS. |
File Servers
The servers and workstations you want to audit should be configured to allow the following connections.
|
CONNECTION |
PORT |
PROTOCOL |
PORT |
REQUIRED FOR |
|---|---|---|---|---|
|
Outbound |
Remote |
TCP |
1433 |
Interaction with Cygna Auditor SQL Server-based data storage. |
|
Inbound |
Local |
TCP |
445 |
Access to the C$ share for agents. |
|
Inbound |
Local |
TCP |
139 |
Only required for networks relying on NetBIOS. |
VMware, Microsoft 365
No specific port configuration is required.