Configure Exchange Server Monitoring
Note: The following applies to Exchange Server versions 2007, 2010, 2013 only.
When you deploy, update, or remove an existing agent from the console application, the mail clients may briefly lose connectivity to the Exchange server and then reconnect automatically. Exchange Agent deployment, upgrade and removal processes will restart the following Exchange-related services, if running:
- Cluster
- World Wide Web Publishing
- Exchange Information Store
- Exchange Replication
- Exchange POP3
- Exchange POP3 Backend
- Exchange RPC Client Access
Agent Requirements
Overview
The agent must be deployed to:
- Exchange 2007 servers with the Mailbox role
- Exchange 2010, 2013, 2016 servers with CAS/IIS/PWS
- Any server that carries mailbox traffic if it is monitored for events
Deployment Requirements
Exchange Server 2007, 2010, 2013
Credentials of the Management Server service account are used to deploy the agents, the account needs:
- Administrator access to the target host and dbo access on the Auditor database
- Remote registry services and DNS name resolution are also required to deploy the agents
- The current user requires enterprise/domain admin access to deploy agents
Exchange Server 2016
In addition to the requirements listed in the codevious section:
Enable Mailbox event auditing
Run the script below in Exchange Management Shell to enable mailbox auditing for each monitored user mailbox:
$mailbox = "username@contoso.com"
Set-Mailbox $mailbox -AuditAdmin $true -AuditOwner @{Add="Update,Copy,Move,MoveToDeletedItems,SoftDelete,HardDelete,FolderBind,MessageBind,Create,MailboxLogin"}
Set-Mailbox $mailbox -AuditAdmin @{Add="Update,Copy,Move,MoveToDeletedItems,SoftDelete,HardDelete,FolderBind,MessageBind,Create,MailboxLogin"}
Set-Mailbox $mailbox -AuditDelegate @{Add="Update,Copy,Move,MoveToDeletedItems,SoftDelete,HardDelete,FolderBind,MessageBind,Create,MailboxLogin"}
How to know if it worked:
Get-Mailbox $mailbox | fl *audit*
Enable Configuration event auditing
By default, configuration (administrator) audit logging is enabled in new installations of Exchange 2016.
Run the following command in Exchange Management Shell to verify logging configuration settings:
Get-AdminAuditLogConfig
Enable WinRM HTTPS listener
The agent requires a WinRM HTTPS listener to be configured on the Exchange 2016 Server.
To verify WinRM configuration, run the following command on the Exchange 2016 Server and check the Client section in the output:
winrm get winrm/config
Configure WINRM for HTTPS, run the following command on the Exchange 2016 Server:
winrm quickconfig -transport:https
For more information about enabling WINRM, please see How To: Configure WINRM for HTTPS at https://support.microsoft.com/en-us/help/2019527/how-to-configure-winrm-for-https.
Agent Service Account
Exchange 2007, 2010, 2013
The agent service account needs local admin on the Exchange server (to audit and act on behalf of users), domain admin access and R/W access to the Auditor database to store events.
Exchange 2016
The agent runs under Local System account. However, the agent requires a separate service account that needs access to Exchange audit logs and to the monitored user mailboxes.
- Create Service Account in Active Directory
- Create a new user account in Active Directory
- Create mailbox for the user
- Create view-only Exchange Role Group
- Create a new Exchange Role Group and add the service account created in Step 1 to the group as follows:
New-RoleGroup -Name "View-only Audit Logs" -Roles "View-Only Audit Logs","View-Only Configuration","View-Only Recipients" -Members "serviceaccount"
For more information, please see the Microsoft article New-RoleGroup.
- Create a new Exchange Role Group and add the service account created in Step 1 to the group as follows:
- Configure mailbox audit logging bypass
- Exclude service account from mailbox audit logging
Note: While reading mailbox audit logs, the agent may generate numerous audit events which may negatively impact the database.
Set-MailboxAuditBypassAssociation -Identity "serviceaccount"AuditBypassEnabled $true - Grant Access to User Mailboxes
- Option 1 (Recommended)
Grant read-only access at folder level.# Script 1 (save as grant_permissions.ps1):
PowerShell Script:[CmdletBinding()]
param (
[Parameter( Mandatory=$true)]
[string]$Mailbox,
[Parameter( Mandatory=$true)]
[string]$User,
[Parameter( Mandatory=$true)]
[string]$Access
)
$exclusions = @("/Sync Issues",
"/Sync Issues/Conflicts",
"/Sync Issues/Local Failures",
"/Sync Issues/Server Failures",
"/Recoverable Items",
"/Deletions",
"/Purges",
"/Versions"
)
$mailboxfolders = @(Get-MailboxFolderStatistics $Mailbox | Where {!($exclusions -icontains $_.FolderPath)} | Select FolderPath)
foreach ($mailboxfolder in $mailboxfolders)
{
$folder = $mailboxfolder.FolderPath.Replace("/","\")
if ($folder -match "Top of Information Store")
{
$folder = $folder.Replace("\Top of Information Store","\")
}
$identity = "$($mailbox):$folder"
Write-Host "Adding $user to $identity with $access permissions"
Add-MailboxFolderPermission -Identity $identity -User $user
AccessRights $Access -ErrorAction
SilentlyContinue
}
# Script 2 (Run from regular PowerShell):
PowerShell Script:
$server="your exchange server name"
$account = "your service account"
$session = New-PSSession -ConfigurationName "Microsoft.Exchange"
ConnectionUri "https://$server/powershell" -Authentication Basic -Credential
Get-Credential
Set-ExecutionPolicy -Scope Process -ExecutionPolicy Unrestricted
Import-PSSession -Session (Get-PSSession -Name $session.Name | Select-Object First 1)
Get-Mailbox -ResultSize Unlimited -Server $server -RecipientTypeDetails
UserMailbox,SharedMailbox | foreach {
c:\temp\scripts\grant-permissions.ps1 -Mailbox $_.Name -User $account -AccessReviewer
}
Remove-PSSession $session
Option 2:
PowerShell Script:
Grant service account FullAccess permissions to read the contents of each monitored mailbox:
$account = "serviceaccount"
$mailbox = "username "
Add-MailboxPermission -Identity $mailbox -User $account -AccessRights
FullAccess -InheritanceType All
Add an Exchange Server for Monitoring
- Start the console.
- Expand Cygna Auditing & Security Suite.
- Expand Auditor for Exchange.
- Right-click the Servers node, and then select New > Agent.
You can also right-click in the working area of the Management Console and select New > Agent.
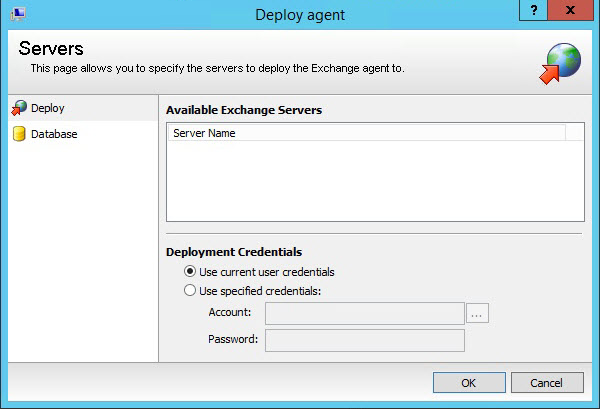
- The Deploy Agent dialog box opens and displays all Exchange Servers that will be monitored. Any servers currently being monitored will not appear in the list.
The agent needs administrative rights on the target machines.
- Click OK to begin monitoring the Exchange Servers.
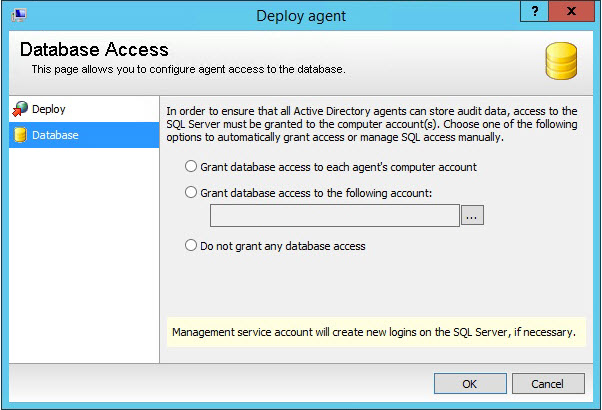
- Select the Database tab. To ensure all audit data can be stored, access to the SQL Server must be granted to the computer accounts. Choose one of the following options to automatically grant access or manage SQL access manually.
- Grant database access to each agent's computer account.
- Grant database access to the following account: Browse to the account.
- Do not grant any database access.
- The servers will now be monitored. Current status will be displayed in the working area.