Tips and Tricks: Including vs Excluding
If you are familiar with the following parts of the "Mastering the Global Search" tutorial—Task: Limiting Search to Specific Events and Task: Excluding Changes from Search—you might be wondering when it makes sense to include parameters to search and when to exclude from search. Though these search techniques are both handy and sometimes can be used interchangeably, here are some tips and tricks that will help you decide which one to use to get your work done more efficiently.
Tips on Excluding—When to Exclude?
Example 1: Excessive events with the same action
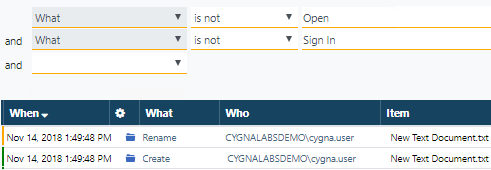
Let's say, you are looking for some suspicious activity (not for specific actions or users!) but excessive numbers of similar events make your data look biased and difficult to review. In most cases, file or folder Open events are the most frequent actions in your environment but they do not facilitate your security investigation. To make things worse, you may fail to notice more important events among them. For example, in the image below, you can see numerous Open events and a single Rename that you can easily miss.
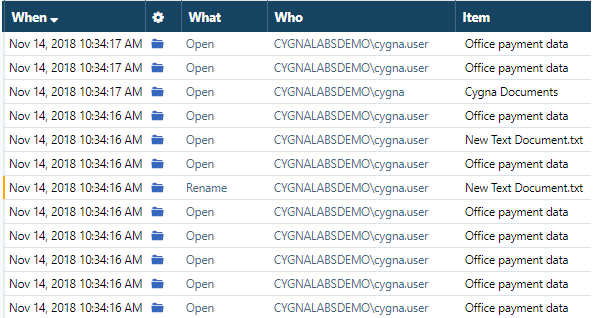
Scrolling down similar events can be overwhelming, try limiting your search to more meaningful records. How can you do that?
- Option 1: Include Rename in your search by clicking the green link. In this case, you'll see only Renames on the screen, the rest of events will be hidden.
- Suggested Option 2: Exclude Open by clicking the red cross next to it. In this example, you'll see only Renames on the screen, all Opens will be hidden. If you had other actions (e.g., create, recycle, write), they would remain on the screen as well.
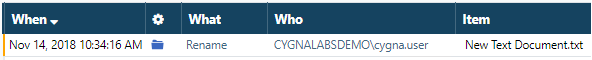
If you are not sure what events you have in your data (because Opens made it so hard to spot them), the safest option is to exclude the excessive action. Thus, you have overall control of actions you exclude. It means that all other events that do not possess this property will remain right in front of you.
Example 2: Similar records are prevailing in the same data column
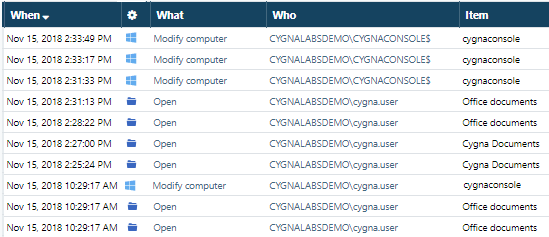
Assume, you see many records with two actions prevailing—this makes your search results difficult to work with. Typically, Sign-ins and Opens are the most frequent events in most organizations but there are more changes to track and review.
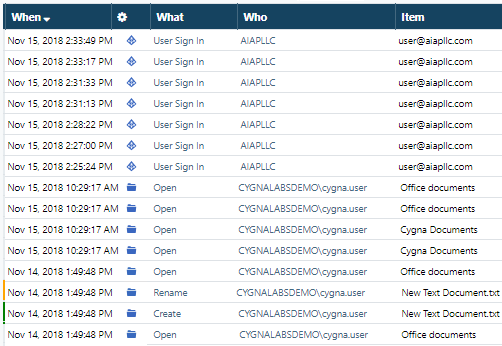
Since you don't know exactly what changes you are looking for, you cannot include them. Including any action to your search will automatically hide all others, not just Sign-ins and Opens. The tip here is to exclude those parameters you don't want to see.
The same logic applies to the Who column. Let's say, you want to review user activity on production file servers but you are overwhelmed by the number of events generated by computer accounts. To ensure that only these accounts are hidden, exclude them.
Example 3: Biased results in multiple columns
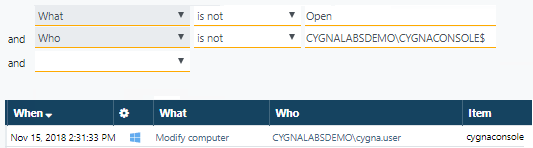
For instance, you are doing a security check-up. On the screen, you see the search results with frequent Opens or computer modifications performed by a computer account. You'll want to hide them and focus on more meaningful data. How can you do that?
Including obviously does not make sense here since you are searching broadly and not for a specific event. If you exclude "Modify computer" and "Open" actions, all records will be hidden that is also not a good way to go since you will toss all computer modifications irrespective of who made them. The best solutions is to mix and match parameters you exclude. You can exclude Opens from the What column and the computer account name from the Who column.
Tips on Including—When to Include?
Example 1: Inspecting user activity and drilling down to suspicious actions
Assume, you have already reviewed activity in your infrastructure, identified potentially harmful events, and now you want to inspect them more closely. This time, you are interested in particular changes. You can start gradually including parameters to your search right from the data area.
Let's say, you want to investigate activity of a certain user as you could not justify some changes this user made. First things first, you want to see what this user did broadly, not only the action that originally drew your attention. Instead of scrolling down your search results and excluding all other users, you should just include this user to the search.
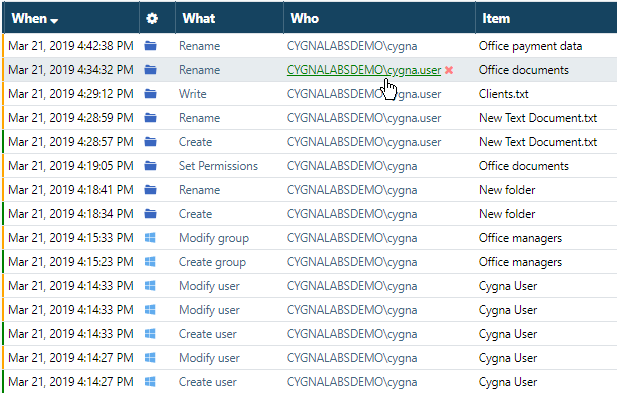
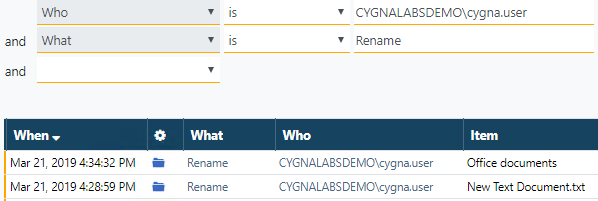
Once the results are limited to this user, you can quickly review them and focus on the most critical changes. For example, you are wondering why the user renamed some files and folders on your file server. Since you are interested in this action only, include it to the search by clicking the green link. In case you are interested in several actions (e.g., rename and create), exclude all actions except those you want to keep on the screen.
Now, you have added two conditions to your search—they work combined as a logical AND and limit your search results to two records that you can easily review in detail.