Task: Mixing & Matching Search Techniques
Goal: Learn how to combine search techniques you mastered in the previous parts of this tutorial.
This part of tutorial recreates a real-life minor security incident with investigation and response from the administration team.
Steps:
-
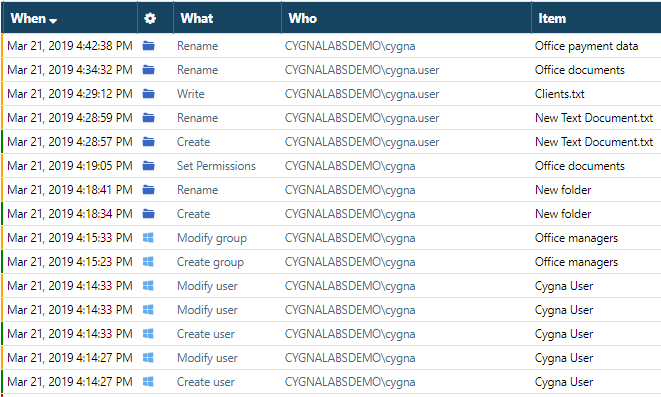
Being a part of administration team, you are in charge of weekly check-ups for Active Directory and File System sources. You browse the records that represent activity in your organization and verify suspicious changes. As always, you start with all changes on your Global Search screen.
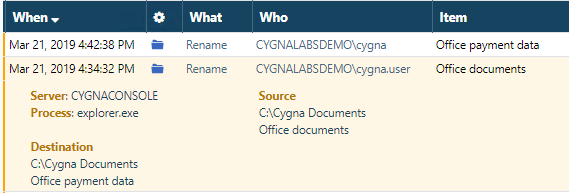
The change related to "Office payment data" attracts you attention. Such names are insecure since they disclose they contain sensitive data the attackers or rogue insiders can take advantage of.
Let's start the investigation and find out more about this folder and activity around it.
-
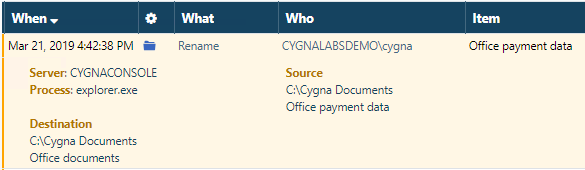
First and foremost, expand the details for this change. As you can see, the "Office payment data" folder was renamed into more reasonable "Office documents" by your company's admin account (cygnalabsdemo\cygna). Looks like the problem has been already mitigated and no response action is required.
For now, you know that administrator renamed a folder that had sensitive name into something less revealing. Likely, the administrator just reverted the changes.
To avoid such issues in the future, you should investigate this case in more detail and rise awareness among your fellow employees that sensitive file and folder names are on the attack surface.
-
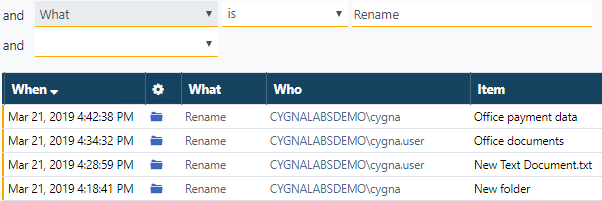
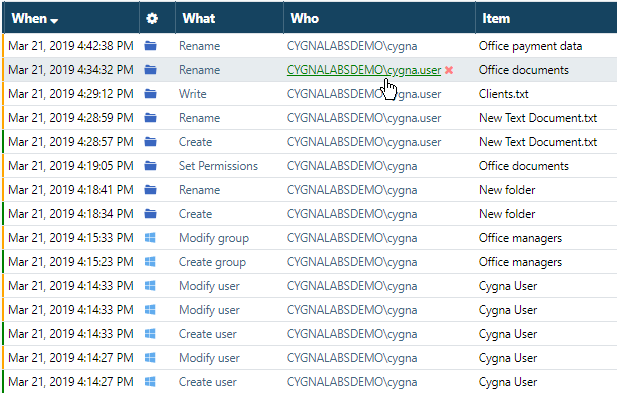
Let's see if there have been more Renames recently. Include Rename in the search either by clicking the green link or by adding a search condition.
-
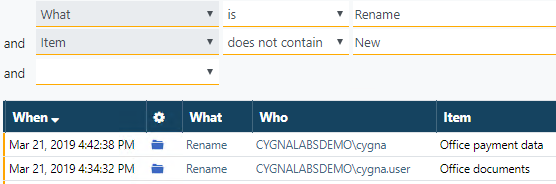
As you know, Cygna Auditor reports adding new objects as Create "New..." with subsequent Rename. These are safe, system-created Renames that can be excluded from inspection. Let's do it—add one more search condition that will exclude records containing "new" in the object name. Make sure to leverage the "does not contain" match type to get broad results.
-
Inspect two records more closely. You have already reviewed the first record so now have a look at the second. As you see, the user "cygnalabsdemo\cygna.user" has renamed the "Office documents" folder into "Office payment data".
Congratulations, now we know who renamed the folder and hinted at business critical data. But does this user rename folders? Is he or she authorized to access this data?
-
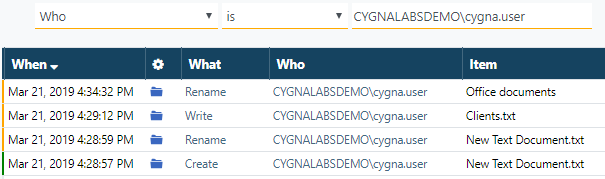
Start by checking recent activity of this user. Delete currently applied search conditions and then include cygna.user in your search.
-
Seems that this user works only with files inside a single folder. For far, we cannot tell if cygna.user is an internal badactor or not. We have to continue our investigation and make sure this user is authorized to access files and folders within the "Office documents" folder.
-
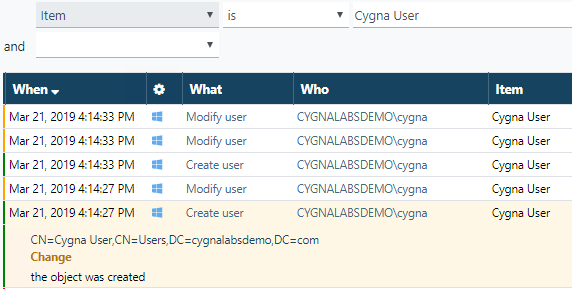
Clear the conditions once again and look for records that mention this user as an object (item). Note, you have to search for display name that is Cygna User. You'll get several records that represent a single event — cygnalabsdemo\cygna (admin) added a new account cygna.user.
Oh, that really makes sense—the administrator could have created a new account for a new employee working with office files. Let's check our guess.
-
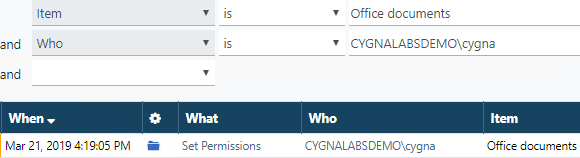
Go forward and check if administrator has modified access permissions for the "Office documents" folder. Bingo! The administrator has recently updated permissions for the exact folder we are reviewing. You can check that "Office managers" Active Directory group is granted the full control permissions on the folder.
-
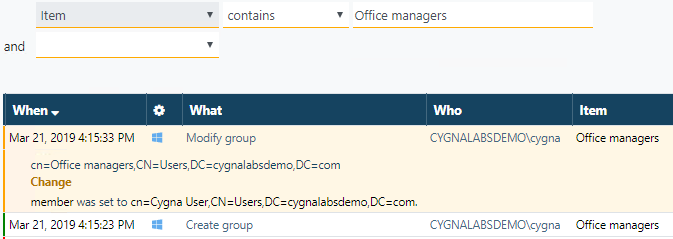
Let's verify if cygna.user is or ever was a member of the "Office managers" group. Update your search, now look for the records with "office managers" as item. You'll find that administrator added cygna.user to the "Office managers" group not so long ago.
Congratulations, investigation completed! All puzzle pieces are in place and now you can see the whole picture. As you found out, the original event chain was as follows: the administrator created a new Active Directory account "cygna.user" and added it to the "Office managers" Active Directory group. Then, the administrator granted full control of the "Office documents" folder to the "Office managers" group. Thus, cygna.user inherited permissions to this folder through group membership and is fully authorized to access office files. While working with files in the "Office documents" folder, cygna.user decided to rename a folder and changed its name to "Office payment data". Cygna, the administrator, noticed the change and reverted to the original folder name to eliminate the risks of disclosing sensitive data.
You investigated the security issue where sensitive data could be disclosed. You unraveled the event chain and now you can evaluate the issue. Based on the current state, no immediate response is required since the issue has been already addressed by cygnalabsdemo\cygna. As a precaution, you can approach cygna.user and explain basic security procedures all employees should follow to avoid potential threats in the future.
Result: You've tried mixing and matching various search techniques while investigating a security issue. As you can see, Cygna Auditor Global Search is universal and there are many ways to achieve the same results. You can always opt for those that make sense in your specific case and combine several search techniques to build queries of any complexity.
Previous parts:
Tutorial: Mastering the Global Search
Task: Reviewing All Changes and Sorting
Task: Limiting Search to Specific Events
Task: Excluding Changes from Search
Tips and Tricks: Including vs Excluding