Active Directory
Active Directory is likely the most critical piece of your IT infrastructure as it keeps your organization together, providing authentication and authorization services, and restricting or allowing access to domain resources. Cygna Auditor helps reduce the potential attack surface by keeping Active Directory activity on the radar.
Cygna Auditor tracks activity across your domains and presents it in a user-friendly format. With Cygna Auditor, you will never miss a new group being created in your domain or a user being promoted to administrator.
Start Collecting Data
- On the Cygna Auditor home page, select Auditor / Configuration / Active Directory / Domains.
- Click
to add a new domain.
-
Complete the domain auditing configuration. Generally, Cygna Auditor provides you with two auditing methods, one employing a non-intrusive monitoring service on your domain controllers and the over relying on event logs.
OPTION
DESCRIPTION
Domain Selection tab
User name
Password
Enter the user credentials. Specify a user name in the following format: domain\username.
Cygna Auditor will use this account to collect audit data from the domains this account has access to. If you specified event log-based auditing, make sure the account has access to domain controllers' event logs.
Domain
By default, the domain where Cygna Auditor is deployed is specified for auditing. To search for other domains in the forest, enter the domain name in the search field and click the loop icon.
Collection Settings tab
Data collection method
Select one of the following:
-
Cygna Auditor Agent (preferred)
-
Event log
Combine similar events occurring within the specified interval
Select this option and set the interval (default, 5000 ms) to reduce the number of events written to the database. For example, when the same user performs the same action multiple times within a short time, Cygna Auditor will make a single entry in the audit database.
If this option is cleared, Cygna Auditor will capture a record for each event.
Attempt to locate workstation information for events
Enable this option to collect originating workstation data—get supplemental information about the workstation from which the action was performed. This information can help troubleshoot security incidents.
Perform reverse name lookup when events only include an IP address for the remote workstation Select to try identifying a DNS name of a remote workstation.
Ignore login events
Select to skip login events from processing.
Enable nested group alerting and auditing
Select this option to report changes to child groups. For example, when a nested group is removed, you will see a change event for the parent group as well. A user removal from a child group isn't reported for a parent group.
Select Manage nested groups and specify groups in the pop-up window. Expand Advanced collector settings to configure additional options for nested group auditing.
Advanced collector settings
Expand this section to configure additional settings if necessary.
-
Exclude attributes from data collection—enter a list of attributes separated by commas.
-
Expanded Auditing
-
Audit LDAP query execution. Capture LDAP query audit event details from the Windows Event Log (if enabled on the domain controller).
-
-
Set up GPO backup configuration, including:
-
Enabling GPO backup for detailed change reporting—with its help you'll be able to see changes in group policy objects over time.
-
Ensuring all GPOs have at least one backup—it gives you ability to see and revert changes at all times.
-
-
If nested group alerting and auditing is enabled, specify details for reporting changes in the Nested group auditing settings section.
-
Process nested changes for non-group objects—e.g., if a user gets removed from a child Group 3, this event will be reported both for child Group 3 and parent Groups 1 and 2.
-
Cascade nested group members when adding a group—e.g., if an intermediate Group 2 is removed, the event is recorded both for the parent Group 1 and its nested Group 3.
-
Cascade nested non-group object members when adding a group—e.g., if an intermediate Group 2 is removed, the event is recorded both for the parent Group 1 and its nested Group 3. For Group 3 users, an event will be generated that they were removed from the top level Group 1.
-
Generate backlink events for nested group changes—by default, events are generated for parent objects. Disable to get events only for child changes.
-
-
Set the logging level. Only change this setting when requested by Support or a Sales Engineer.
Collection Schedule (Event Log only) tab
Create a colection schedule
Create a schedule to define the frequency for Event Log collection.
-
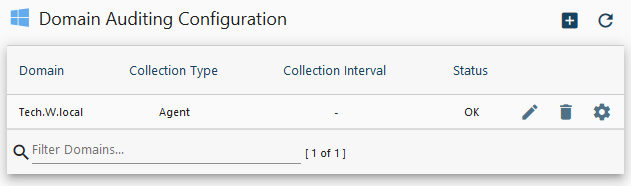
The domains you configured for auditing will appear in the list, with the status and data collection frequency for each domain. Click on the pencil icon to edit collection settings. Click on the trash can icon to stop auditing the domain. Click on the library icon to view domain controller status and manage domain controller agents for the domain.
Manage Domain Controllers
The Manage Domain Controllers page allows you to manage the deployed Active Directory audit services on your domain controllers. Domain Controllers may be tagged
with custom tags to facilitate update groups. Use the 
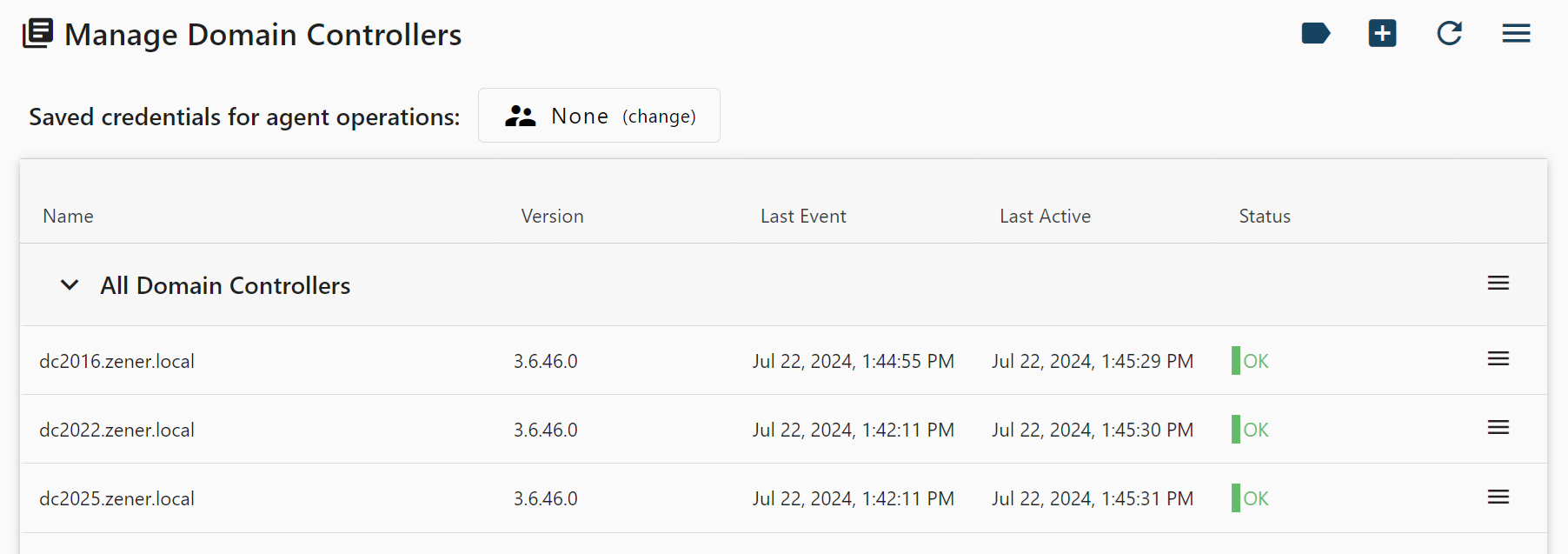
The 

If operations must be performed by an alternate user, enter the credentials in the Saved credentials for agent operations section near the top of the page. Note that these credentials will be saved for later operations but may be cleared or edited by returning to this screen.
Note: This step is only required if you use Windows authentication on your SQL Server.
To ensure the agent feeds audit data to your Cygna Auditor database, make sure it has sufficient permissions on your SQL Server instance.
For each domain controller where the agent runs, do the following: On SQL Server, create a login for each computer account (domain\computeraccount$) and assign it the db_owner and public roles for your Cygna Auditor database.
Continue reading:
Configuring Collector Settings
Configuring Password Expiry Alerts
